Manage User Access Control
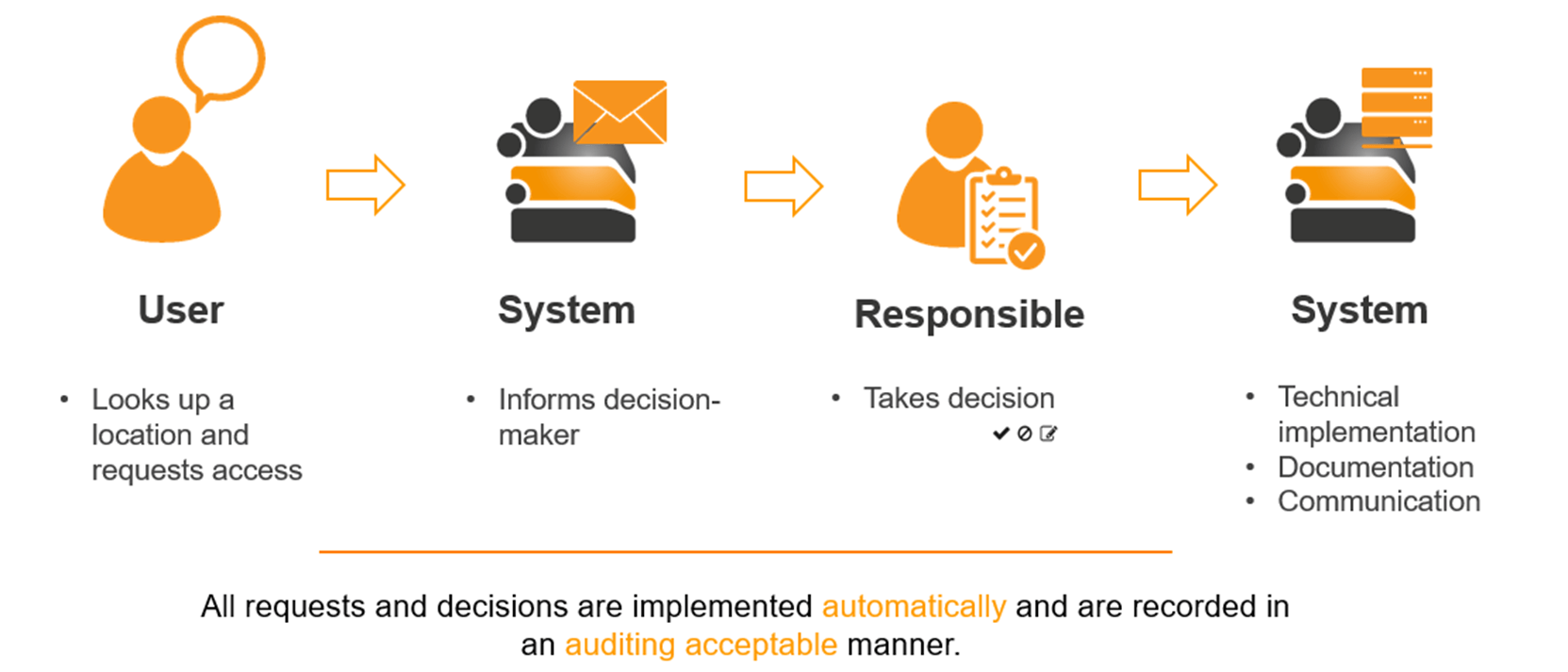
Effectively manage user access control to ensure that only authorized personnel have access to critical systems. This includes setting up user accounts, assigning appropriate permissions, and regularly reviewing access rights. By creating role-based access control (RBAC), users can be assigned specific roles that limit their access to only the resources necessary for their job. Regular audits should be conducted to remove unnecessary accounts or adjust permissions for users who change roles. The system manager is also responsible for integrating authentication systems such as multi-factor authentication (MFA) and monitoring for any unauthorized access attempts. This tight control over user access reduces the risk of security breaches and data loss.


Reviews
There are no reviews yet.